How can a visitor management system help with HIPAA compliance?

It may finally be "game over" for old-fashioned logbooks at hospitals, insurance agencies, for other key players in the healthcare industry overall.
The time for improving security and regulatory compliance by using a visitor management system is now. Why?
Because of the need to be HIPAA-compliant, and to protect healthcare information.
And it all comes down to data privacy.
Prior to HIPAA, no generally accepted set of security standards or general requirements for protecting health information existed in the health care industry.
At the same time, new technologies were evolving, and the health care industry began to move away from paper processes and rely more heavily on the use of electronic information systems...
This notion of data privacy isn't new. Yet figuring out how visitor management fits into HIPAA compliance still raises questions.
This articles aims to answer some of those questions to help you on your way to choosing a HIPAA-compliant visitor management system for your business.
What is HIPAA?
HIPAA stands for Health Insurance Portability and Accountability Act.
It was created to protect the flow and maintenance of healthcare information, namely, the Personally Identifiable Information of individuals seeking healthcare and healthcare insurance.
Personally Identifiable Information (PII) includes, but is not limited to, the following:
- Names (Full or last name and initial),
- Phone and/or fax numbers,
- Email addresses,
- Vehicle identifiers (including serial numbers and license plate numbers)
- Specific geographical identifiers,
- Dates (other than year) directly related to an individual,
- Social Security numbers,
- Medical record, health insurance account and/or beneficiary numbers,
- Device identifiers and serial numbers,
- Web URLs and/or IP address numbers,
- Full-face and/or comparable images,
- Biometric identifiers such as finger, retinal and voice prints, etc.,
The Health Insurance Portability and Accountability Act of 1996 (HIPAA) required the Secretary of the U.S. Department of Health and Human Services (HHS) to develop regulations protecting the privacy and security of certain health information.
To fulfill this requirement, HHS published what are commonly known as the HIPAA Privacy Rule and the HIPAA Security Rule.
So let's take a quick look at the HIPAA Privacy Rule and Security Rule...
What is the HIPAA Privacy Rule?
The Privacy Rule's goal is to assure that individuals’ health information is properly protected while it's being sent here and there, as is the business norm these days. This flow of information is needed to provide high quality health care and to protect the public's health and well being.
But this shouldn't come at the expense of the privacy of those seeing treatment or help.
Data and privacy around data is a human right and has to be protected. You have to be transparent about it.
— Satya Nadella, Microsoft CEO, World Economic Forum's Annual Meeting 2020
Who is covered by the Privacy Rule?
The HIPAA Privacy Rule applies to health plans, healthcare clearinghouses, and to any health care provider or their business associates who transmits health information in electronic form—all considered a "covered entity."
For example, if you own a massage therapy business then chances are that HIPAA doesn't apply to you (though it's always better to be safe than sorry).
However, you can always double-check if your business falls under HIPAA's jurisdiction to be sure.
What is the HIPAA Security Rule?
The same covered entities are HIPAA Security Rule, also subject establishes the standards for protecting personal health information that is held or transferred electronically. It addresses the safeguards that “covered entities” must put in place to secure individuals’ “electronic protected health information.” (e-PHI).
According to the U.S. Department of Health & Human Services, The Security Rule requires businesses to follow four general rules:- Ensure the confidentiality, integrity, and availability of all e-PHI they create, receive, maintain or transmit,
- Identify and protect against reasonably anticipated threats to the security or integrity of the information,
- Protect against reasonably anticipated, impermissible uses or disclosures, and
- Ensure compliance by their workforce.
Further more, there are three parts to the safeguards that covered entities must put in place for the protection of said personal health information:
- Technical safeguards,
- Physical safeguards, and
- Administrative safeguards
This means that processes must be put in place so certain areas of the facility can be regulated and kept off limits to visitors. This is where a solid visitor management system can definitely help. Because it's your duty as a HIPAA compliant company to prevent unauthorized physical access to Protected Health Information (PHI).
Physical security versus network security
Security is a two-pronged undertaking. You have to put in place robust network security in the office (see how Poxyclick handles security) including, but not limited to:
- establishing firewalls,
- encrypting data,
- implementing escalation policies,
- running background checks,
- securing servers, and
- earning external validations and certification (e.g. SOC 2 Type II certification, Cloud Security Alliance CAIQ, and third-party penetration testing)
In addition, having physical safeguards and security in place is just as important, and a huge part of being HIPAA-compliant.
How can a visitor management system help with HIPAA compliance?
This is where the aspects of physical security come in.
As much as welcoming visitors and contractors on your premises is a business norm, these same people pose high risks where data privacy are concerned.
But digital visitor management systems can take your security to a whole new level, starting right at the front desk.
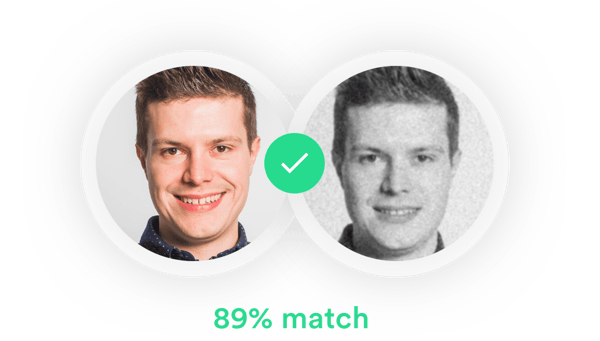 From pre-screening who comes in and around your building at all times to verifying identities using facial recognition, and checking their names against global watchlists, it's now easier than ever to restrict access to certain parts of your premises.
From pre-screening who comes in and around your building at all times to verifying identities using facial recognition, and checking their names against global watchlists, it's now easier than ever to restrict access to certain parts of your premises.
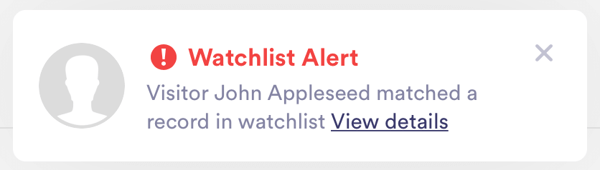 And it can all be done discreetly and safely so that each visitor experience is a seamless and memorable one.
And it can all be done discreetly and safely so that each visitor experience is a seamless and memorable one.
These are all integral parts of what a cloud-based visitor management system like Proxyclick can do for you.
What are the risks of not being HIPAA-compliant?
Within the U.S. Department of Health & Human Services, the Office for Civil Rights (OCR) has responsibility for enforcing the Privacy and Security Rules with voluntary compliance activities and civil money penalties.
Among their responsibilities:
- Providing the ability to transfer any health insurance coverage for millions of American workers and their families when they change or lose their jobs,
- Reducing health-care fraud and abuse,
- Mandating industry-wide standards for health care information on electronic billing and other processes, and
- Requiring the protection and confidential handling of protected health information.
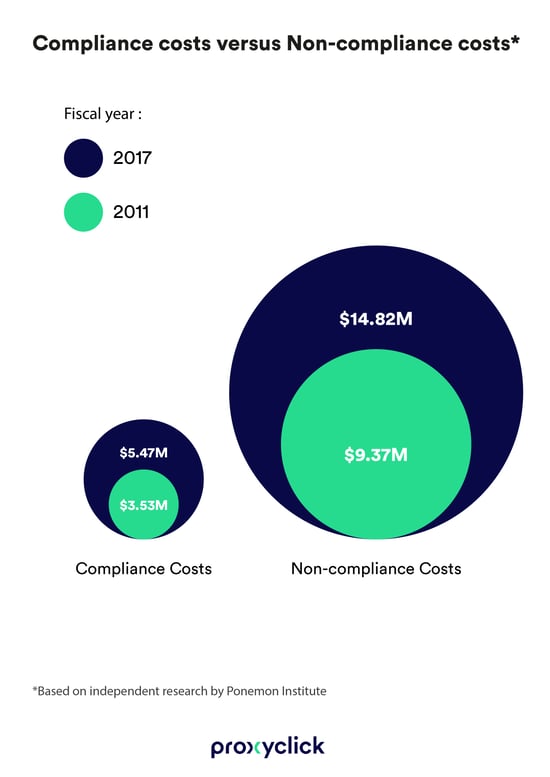
With the cost of non-compliance spiking nearly 50% since 2011, can your company afford not to stay on the right side of regulations?
 At Proxyclick, data privacy has been at the core of our business from the start. So it's part of our day-to-day to help those organizations seeking HIPAA compliance find the right balance between security and data privacy.
At Proxyclick, data privacy has been at the core of our business from the start. So it's part of our day-to-day to help those organizations seeking HIPAA compliance find the right balance between security and data privacy.
For more on other regulations and compliance-related information, we recommend you head over to our regulatory compliance guide. Or go ahead and sign up for a free trial of our solution, and see how Proxyclick can meet your needs.
***
Disclaimer: The information presented above is not legal advice, is not to be acted on as such, may not be current and is subject to change without notice. You should seek professional legal counsel before taking any action.


